Top 10 Least Vulnerable to Malware Operating System 2018
Government agencies amongst others. The Buggy Web Application or BWAPP is a great free and open source tool for students devs and security pros alikeIts a PHP app that relies on a MySQL database.

2021 Ransomware Attack List And Alerts Cloudian
Whether youre preparing for a project or just want to get some practice in to keep your ethical hacking skills up to par this solution with the cute and happy little bee mascot contains more than 100.

. The subscription-based malware service Prometheus TDS was first discovered in August of 2021 by Group-IB as part of an email campaign targeting US. The Crimeware-as-a-Service CaaS offering was posted by a cyber threat actor called Ma1n on various Russian hack forums to a primarily Russian customer base.

Atos Blog Log4shell Unauthenticated Rce 0 Day Exploit

It Threat Evolution Q1 2018 Statistics Securelist

Do Macs Need Antivirus Or Is Built In Protection Enough
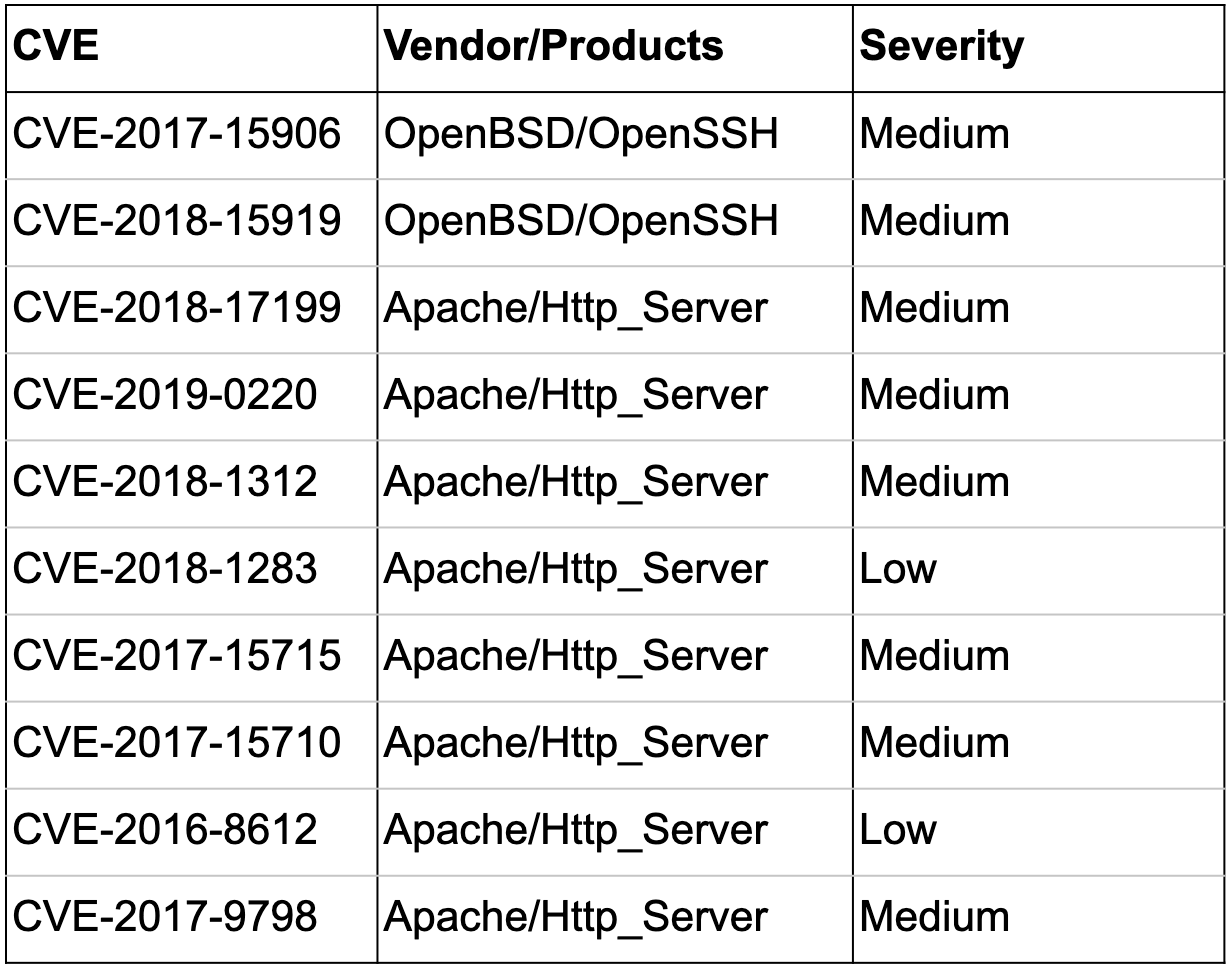
Hunting The Public Cloud For Exposed Hosts And Misconfigurations

7 Types Of Cyber Security Threats
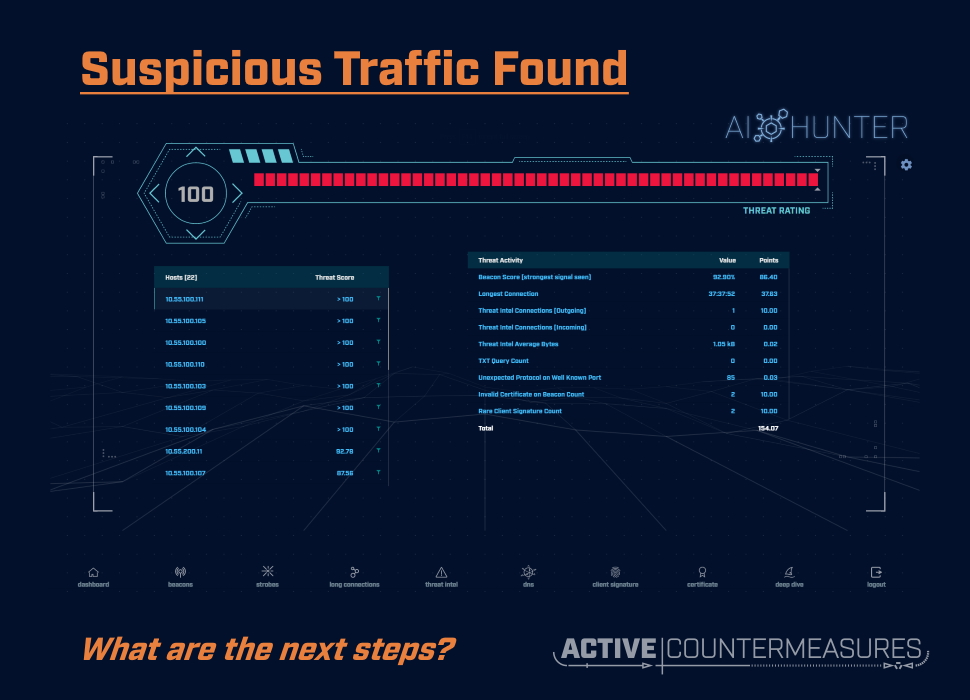
Suspicious Traffic Found What Are The Next Steps Active Countermeasures

Hunting The Public Cloud For Exposed Hosts And Misconfigurations

Ransomware Groups Continue To Target Healthcare Critical Services Here S How To Reduce Risk Microsoft Security Blog

Pdf Malware Detection Issues And Challenges

Data Breach 101 Top 5 Reasons It Happens Whoa Com
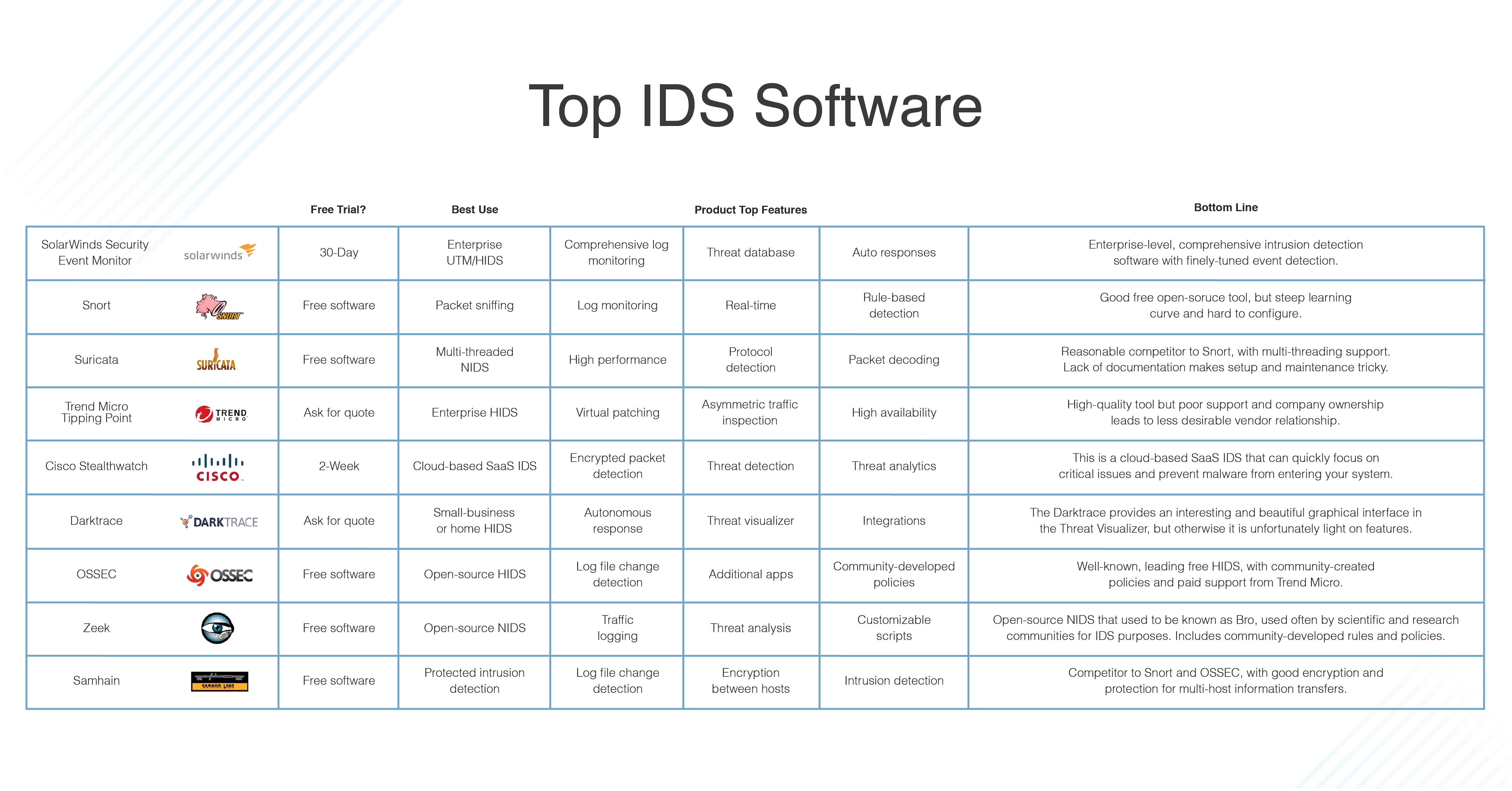
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff
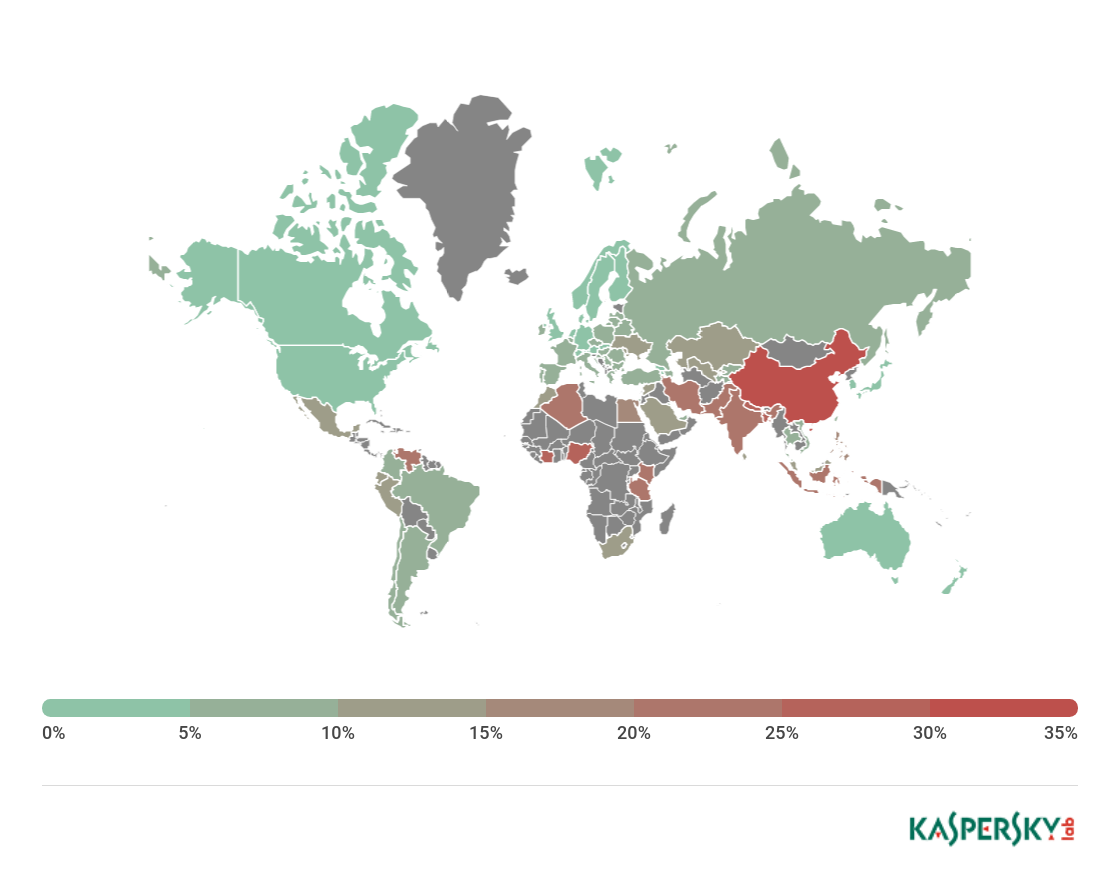
It Threat Evolution Q1 2018 Statistics Securelist
Electronics Free Full Text Magniber V2 Ransomware Decryption Exploiting The Vulnerability Of A Self Developed Pseudo Random Number Generator Html

Do Macs Need Antivirus Or Is Built In Protection Enough
![]()
Ranked Best Browsers For Privacy In 2022 Expressvpn Blog

Tools And Techniques For Collection And Analysis Of Internet Of Things Malware A Systematic State Of Art Review Sciencedirect

0 Response to "Top 10 Least Vulnerable to Malware Operating System 2018"
Post a Comment